Ask a simple question and save thousands!
A true story: When hackers go ‘whaling’ they know that most people are too nervous to ask the simplest of questions.

A true story: When hackers go ‘whaling’ they know that most people are too nervous to ask the simplest of questions.
“What shocked me the most,” said the CEO of a major firm, “was that no one thought it sensible to just personally ask me or the Financial Director about those demands for immediate payment!”
And the question he wanted to be asked? ‘Did either of you authorise this really big payment to a supplier?’
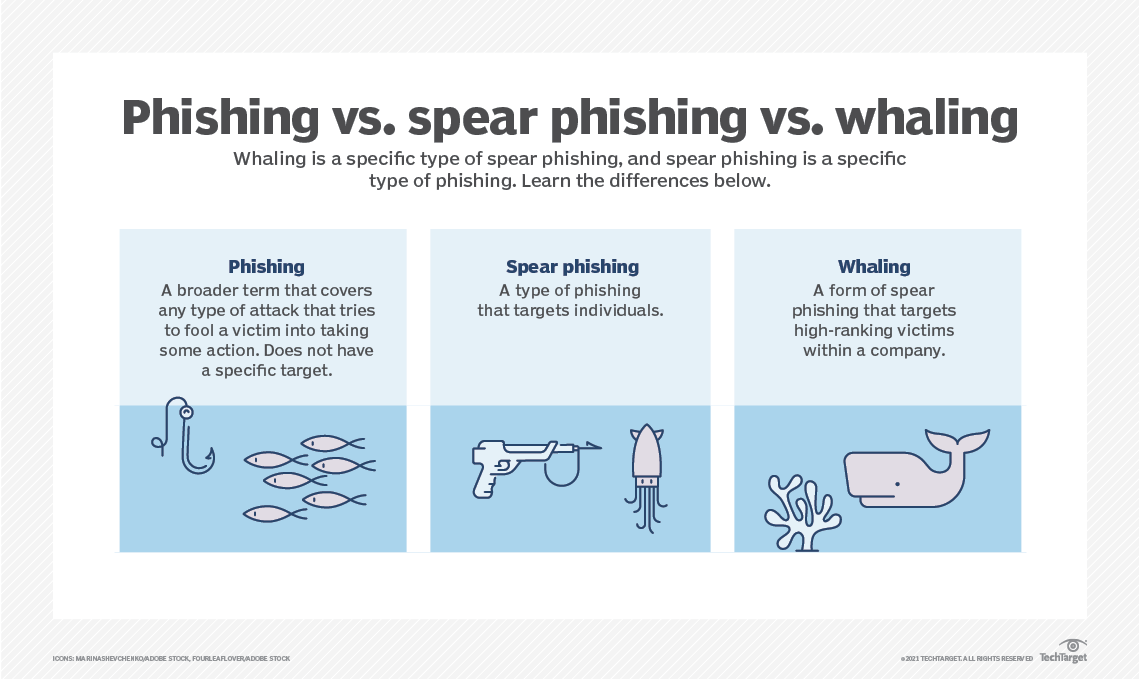
The CEO and the Financial Director were ‘whales’ – important officers in an organization who had not only the authority to authorise payments, but also access to all the secrets and data within the business. They’re really big fish, the whales. Hackers spend lots of energy and use ingenious social engineering techniques to either steal data or get ways to pretend to be those people online.
So, they hack into the company systems, spoof emails, steal credentials, and then intercept information so that they can use it to steal money or intellectual property. In this case the object was purely financial. This is how it worked.
The CEO and his board decided they’d employ a specialist recruitment agency to find an ideal candidate for a vacancy in the C-suite. They agreed to hire an agency they’d worked with before and vowed them (and everyone else) to secrecy. They didn’t want the business or the market to know that they were looking at candidates.
The hackers had already managed to get into the firm’s systems and could read emails between the CEO and the Finance Director, and between both of them and their executive assistants. When they discovered the secret project they knew they could exploit it. So, they spoofed both the CEO’s and FD’s email as well as the recruitment agency’s headed notepaper and email address, and then sent one of the assistant’s an invoice (in PDF form) for £40,000. The email said that it needed to be paid right away. When the assistant emailed the FD to check whether she knew about the invoice, the email went to the hackers. They replied saying that it was authorised. The invoice went to Accounts Payable and, because it wasn’t out of the ordinary, it was quickly settled.
The hackers were encouraged. They quickly got greedy – as hackers tend to do when they’re on to a good thing. So, they sent in a new invoice, this time asking for a whopping £434,000. The FD’s assistant thought this was a bit strange. The hackers argued it was a bill that had been overlooked. But the assistant emailed the CEO’s assistant to ask if they knew anything about it. The CEO’s assistant sent an email to his boss. But the hackers intercepted that too and swiftly replied that the bill was legitimate. The FD’s assistant then decided to check again with her boss. The FD was at a conference, so the assistant texted her. She missed it. The assistant was still uncertain, so she sent an email to the Group HR Director to check whether such a large bill was normal from a recruitment agency.
The hackers were watching. They then sent an email in the FD’s name with an angry message telling the assistant to, basically, stop messing about and get this invoice paid. So, the assistant passed it on for payment. When accounts sought confirmation directly from the FD, the hackers spoofed her assent.
Greed always leads to… more greed. The hackers decided this was just too easy. So, a month later, they emailed the firm’s Accounts Payable team with a stiff message that seemed to come from the recruitment agency’s accountant stating that the 400k had not turned up and to send it again!
It was only at that point anyone actually asked a question of the FD in person. She was called out of a board meeting and was shocked to discover that the original invoices had been ‘authorised’ in emails that purported to come from her! The FD contacted the CEO and immediate action was taken by the firm’s security team (who were belatedly informed) to recover the funds and lock down the emails of all board members.
What went wrong?
So, the CEO resolved to change that situation:
“We all know we’re whales now. And we’re rolling out simple and engaging training to help our people understand the threats, spot anything unusual and, most importantly, ask simple questions.”
“My door is always open, and so are the doors of the entire leadership team. At a time when many of our staff are working from home either all or part of the time, our systems are more vulnerable to attack, so we need to address that not just with technology but with very human techniques: if you’re suspicious say something, ask simple questions, and never just accept an email as authorisation for large payments or transfers of data.”
Whaling (for the big honcho), Spear phishing (for middle management) and phishing (for the rest of us) go on all the time. Be vigilant. Ask questions. Check the email from someone you know is really from someone you know, especially if it demands money, and everything will be a lot more secure.